25. January 2021 By Arman Kohli
Putting the ISO 2700x series to the (practical) test
Security is one of the central requirements for IT services. Security is always changing, which is why work on the level of security you have should never stop. The changing and increasing requirements should be assimilated and considered just as often as awareness measures on security topics should be offered to the employees of a company.
Continuously developing your information security management system (ISMS) based on existing standards and tailored adjustments can lead to the information being used securely in the long term.
In principle, information security is based on the three protection objectives: confidentiality, availability and integrity. Companies can ensure a high level of security if they view creating information security as a continuous process rather than a project with a set completion date. The adequacy and effectiveness of all of the elements of the ISMS need to be reviewed on an ongoing basis. This means that not only do individual security measures need to be reviewed, but also that the company’s security strategy should be regularly revisited and expanded upon.
A number of standards, policies and guidelines have been created to defend companies against the dangers posed by cyber attacks. They are designed to help them integrate information security into their operations. The internationally recognised ISO 2700x series of standards is well-known in the information security world. These types of standards are designed to serve as a guide for companies, but don’t set out concrete processes or recommendations for action.
Overview of ISO norms and standards
The most important standards for information security management systems are those of the International Standards Organisation, which are grouped in the 2700x series of standards. The standards relevant for ISMS are grouped together and new standards are developed under a consistent numbering system, beginning with 27.
ISO 27000 provides a general overview of information security management systems and the interrelationships of the various standards in the ISO 2700x family.
ISO 27001
Due to the complexity of information technology and the demand for certification in recent years, numerous guidance documents, standards and national norms on information security have emerged. The ISO standard 27001 ‘Information technology – Security techniques – Information security management systems requirements specification’ is the first international standard for the management of information security to also enable certification. ISO 27001 includes general recommendations, including how to introduce, operate and improve a documented information security management system, while also taking the risks into account. As a reader, however, you don’t get any help in terms of practical implementation in this standard.
ISO 27002
The aim of ISO 27002 ‘Information technology – Code of practice for information security management’ is to define a framework for information security management. ISO 27002 is therefore mainly concerned with the steps required to establish a functioning security management system and to anchor it in the organisation. The recommendations are primarily intended for management level and contain little concrete technical advice. Implementing the security recommendations in ISO 27002 is one of many ways to meet the requirements of ISO standard 27001.
ISO 27005
The ISO 27005 standard ‘Information security risk management’ contains framework recommendations for risk management for information security. Among other things, it supports the implementation of the requirements set out in ISO 27001. However, it does not specify a risk management method.
ISO 27006
ISO 27006 ‘Information technology – Security techniques – Requirements for the accreditation of bodies providing certification of information security management systems’ specifies requirements for the accreditation of certification bodies for ISMS and also deals with specifics of ISMS certification processes.
The ISO 2700x series of standards is expected to consist of ISO standards 27000 to 27019 and 27030 to 27044. All standards of this series deal with different aspects of security management and relate to the requirements of ISO 27001. The other standards should contribute to a better understanding of ISO 27001 and help to apply it in practice. For example, ISO 27011 deals with the requirements and challenges of telecommunication service providers and ISO 27019 specifically deals with the requirements and challenges of energy providers.
ISMS risk management
The core aspects of an ISMS include identifying, analysing and considering security-relevant events and developing and implementing appropriate protective measures. These are typically:
- Dealing with risks, vulnerabilities and gaps in security.
- Providing guidelines and instructions.
- Planning and implementing concrete security measures.
- Reviewing different products, services or structures via audits, among other things.
- Allocating responsibilities.
According to ISO standards, the characteristics of an ISMS include 14 security topics, which lead to 35 action goals and a total of 114 security requirements.
The scope of duties also includes the management of any kind of assets an organisation has. These include information, software, computer programs, tangible assets such as computers, services, employees and their qualifications, skills, experience and intangible assets such as reputation and standing.
Guidelines are general intentions and instructions formally issued by management. These should be developed with the appropriate experience and knowledge and coordinated with all stakeholders. Processes are sequences of interrelated or interacting activities that deliver specific results to defined inputs. Procedures are defined as predetermined ways of explaining how an activity or process is to be carried out.
The direct link to the company’s objectives is intended to facilitate management decision-making and create transparency. Using an extended ISMS as risk management therefore provides important information and assessments for management.
Even the annual status report on IT security published by the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, BSI) illustrates the variety of new attack techniques and scenarios as well as malware variants. The most serious methods of attack include identity theft, botnets and other social engineering attacks, as well as successful technical attacks such as distributed denial of service (DDoS) attacks, malware attacks, phishing, ransomware and attacks by exploiting modern processor architecture.
There is also a growing trend towards more artificial intelligence (AI) across industries and sectors. In terms of information security, while AI can help detect and combat attacks in an automated way, it can also be misused as an attack tool itself. This means that this and other technologies should be continuously analysed by IT experts and assessed with regard to the potential threats they could pose. The threat level for companies is not only high, but is growing quickly. Extending an ISMS with subject matter expertise beyond the standards therefore creates competitive and cost benefits.
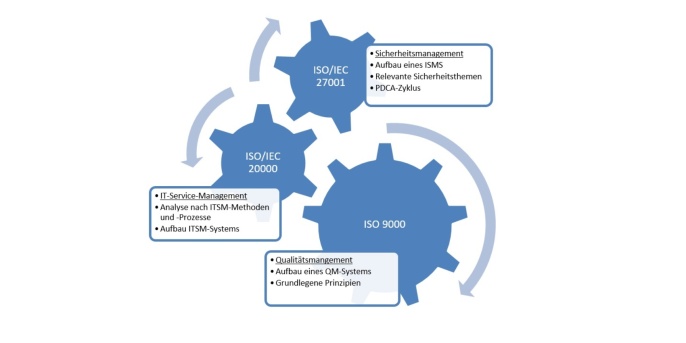
Companies can also use synergy effects to certify their own company according to ISO 20000 (IT service management) or ISO 9000 (quality management) on top of the certification according to ISO 27001 (ISMS). By applying and combining these related standards, all of the processes and organisation can be improved in a sustainable and goal-oriented manner. This creates crucial advantages for and improves the reputation of the company itself with almost half the effort.
The ISO 20000 standard enables companies to be certified according to IT service management. This standard is an international standard that defines the minimum requirements for IT service management. Among other things, it requires evidence of a continuous improvement process and an integrated process approach that enables IT services to be delivered effectively. ISO 9000 certifies the company’s quality management.
Would you like to learn more about exciting topics from the world of adesso? Then check out our latest blog posts.
By the way, adesso ensures that companies receive the best possible security. Click the link to find out everything you need to know about our service packages.

